Released in the latter half of 2013, CryptoLocker is a new threat that takes your files hostage by encrypting them and demands that you pay to have the unlock key sent to you. In short this is ransomware and at the present time they are getting away with it. Even local police departments are paying the ransom to have the files unlocked. From my point of view and those of many others, this is the nastiest virus/malware/ransomware ever released. No anti-virus or anti-malware will be able to decrypt the files and the only solution at present, is to pay the ransom. But there is a way to protect you from CryptoLocker, and other similar threats, by keeping off-line backups of all your important files.
First, what exactly is CryptoLocker?
This type of malware denies the user access to his files or the normal use of his computer. They demand payment, sometimes by untraceable Bitcoin, to restore the computer to the state it was in before the infection. This particular one looks for files with certain extensions and encrypts them. The targeted files have the extensions:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx
You will know you are infected when you see this pop up window:
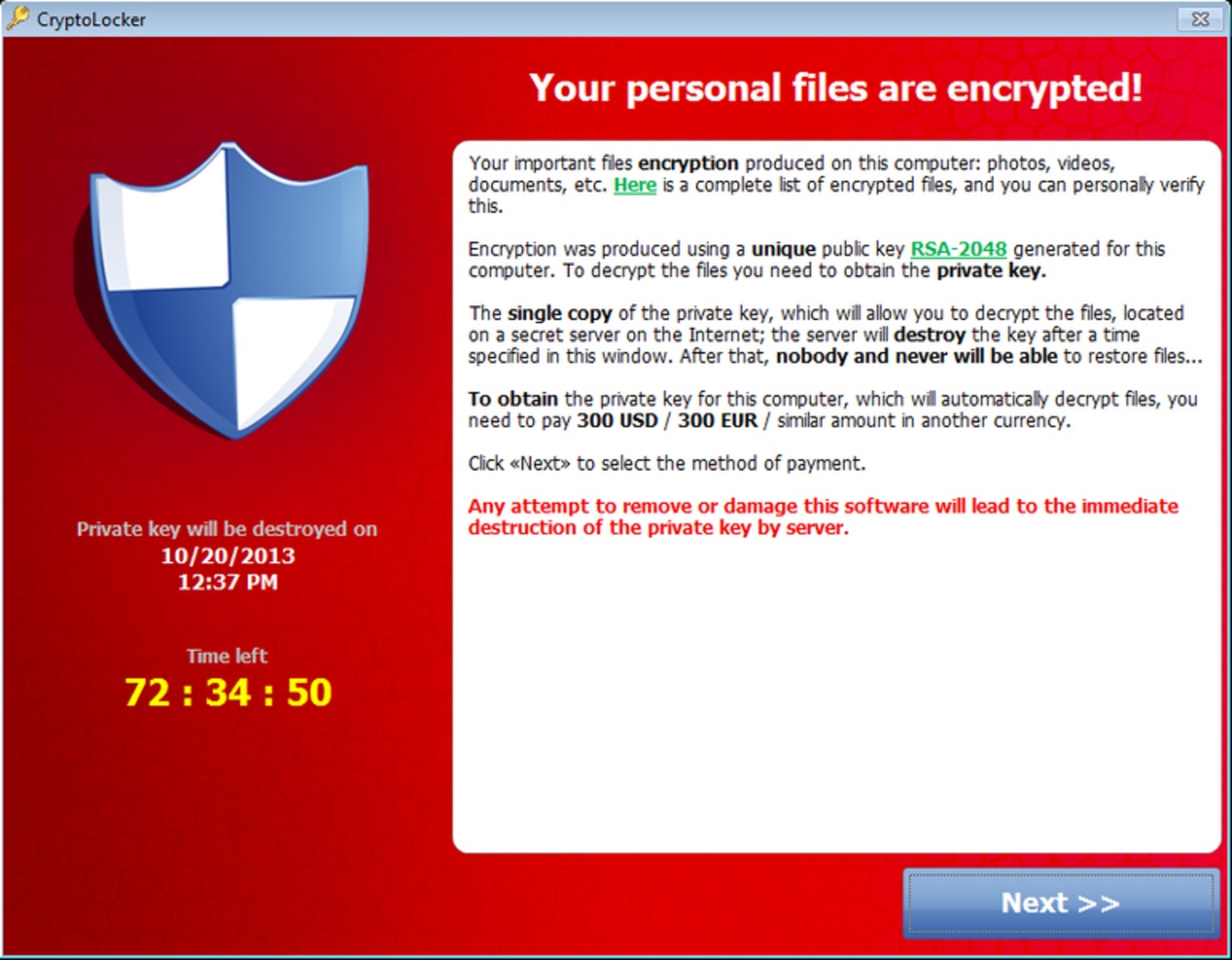
How does Cryptolocker get on my Windows computer?
Ransomware uses different methods for spreading themselves; mainly you will see them as an attachment in a fake email or it is also spread by websites that you visit. So be sure to stay extra careful while searching and browsing the web. Google, Bing, Yahoo are pretty good at detecting if sites are suspicious and will let you know from the search results. But take that extra second to see what you are clicking on from the search engines. The same goes for email.
Steps To Take To Prevent a CryptoLocker Attack
First, use a reputable anti-malware or anti-virus products. Malwarebytes, Avast!, and Symantec are all good ones. They will stop the infection before it has a chance of activating.
Secondly, use For Safety Sake On-Line Backup software that makes a remote backup of all your personal data files, such as photos, documents, email, etc to the For Safety Sake data cloud. All of your data is fully secured by an encryption key that only you have. Also remember that if you have multiple users on your computer to also backup their settings and software as well. We offer a free service that will verify all the right files are being backed up, just give us a call.
If you are really security conscious you can also use our software to create a full backup of your entire computer to a local USB drive so that you have a barebones backup of everything. But remember to unplug that USB drive so it is not infected as well if you get attacked.
If you get infected by the CryptoLocker virus DO NOT pay them as you will just be encouraging future behavior like this. Call us as your first line of defense and be rest assured that you can wipe your computer, reinstall your software and restore all your data from the For Safety Sake Cloud.
Note that if you have already been infected, then it’s too late. Take these low cost preventive steps to stay clear of this new form of ransomware.

